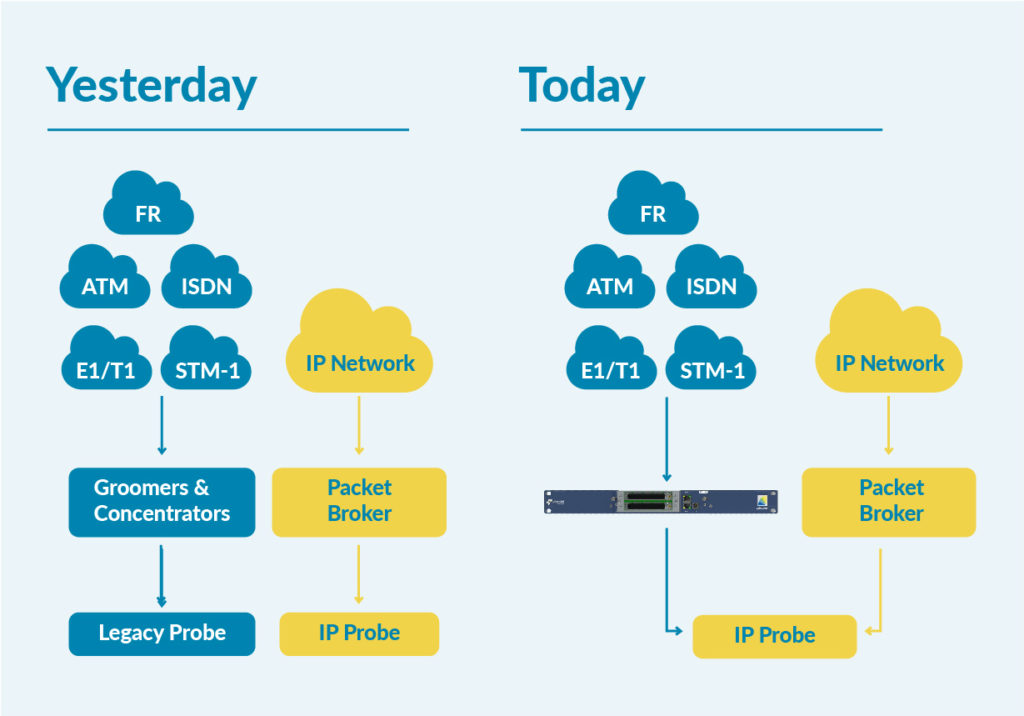
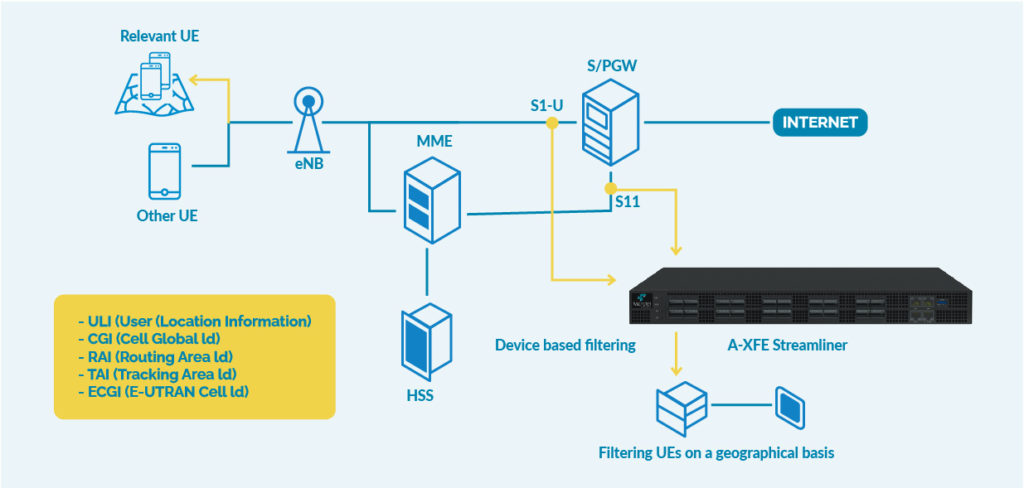
5G deployments are moving beyond enhanced mobile broadband and fixed wireless access and are beginning to enable a wider range of use cases.
5G is the 5th generation mobile network: it is designed to connect virtually everyone and everything together including machines, objects, and devices. 5G wireless technology is meant to deliver higher multi-Gbps peak data speeds, ultra-low latency, more reliability, massive network capacity, increased availability, and a more uniform user experience to more users.
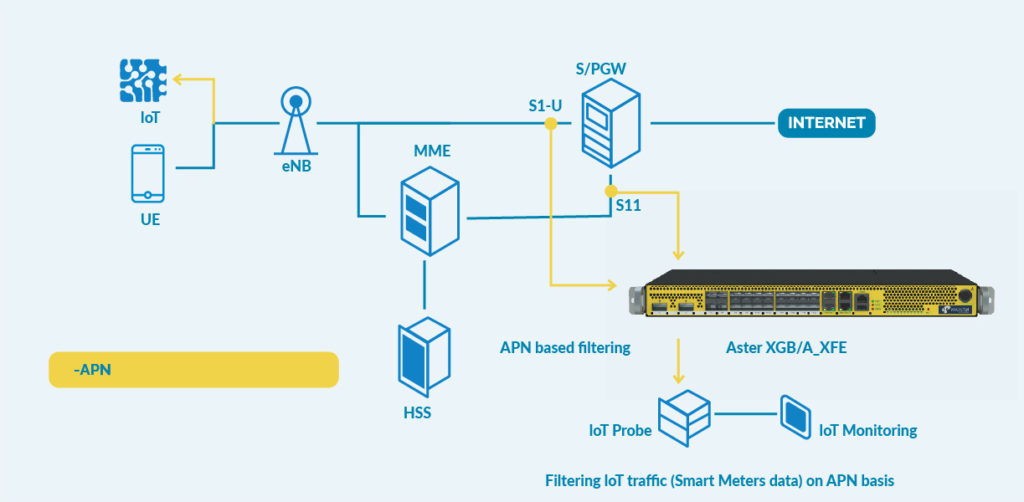
But: what about 5G Network Visibility? New challenges must be solved, and Microtel Innovation is here to help.

The user plane traffic is continuously growing
Mobile traffic is growing more than expected, this is a clear trend of the past decades, and 5G networks will only accelerate it. Consumers and business users worldwide continue to create new demands and expectations for mobile networking. This ongoing trend is clearly highlighted by the adoption and use of mobile applications: social networking, video streaming and downloads, business productivity, e-commerce and gaming will drive the continued growth of mobile traffic.
According to the latest Ericsson Mobility Report, global mobile data is estimated to reach around 680EB per month by the end of 2021, and is projected to grow by a factor of around 4.6 to reach 370EB per month in 2027.
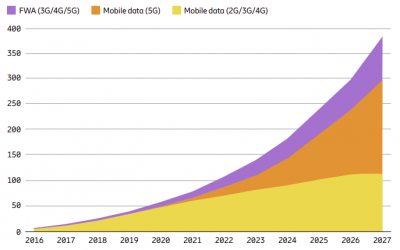
Global mobile network data traffic (EB per month)
How to handle all this traffic, in the Monitoring and Security space?
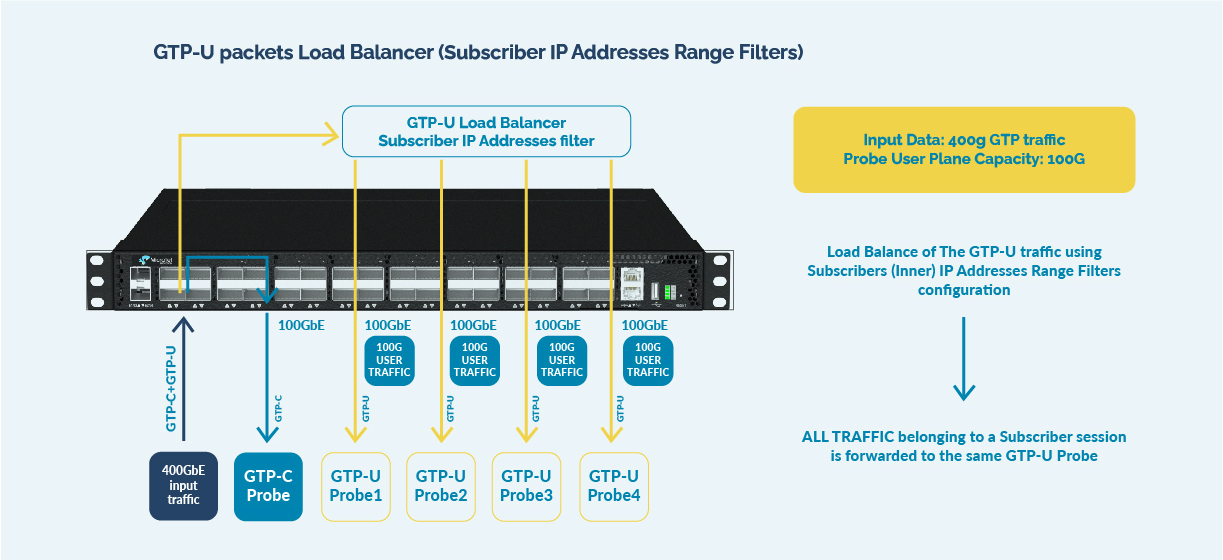
Microtel Innovation new Packet Brokers A-640 are the solution: they support session based traffic balancing to the security and monitoring tools, thanks to their capability to forward the traffic based on inner packet parameters. This is a key task to enable high volume user plane analysis. And they are future proof solutions: no problems with the growing traffic, since A-640 NPB can manage up to 3.2 Tbps of traffic.
More information at https://www.microtelinnovation.com/solutions-archive/5g-user-plane-balancing/.
Big infrastructure vendors tent to use their virtual TAP to provide virtual traffic to be monitored
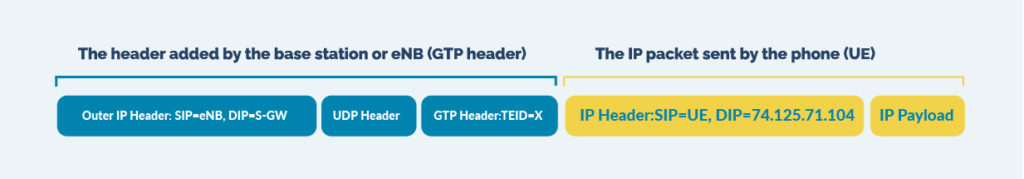
One challenge with the 5G Service-Based Architectures (SBA) is the encrypted nature of the communications between the 5G Core Network Functions.
NEM are proposing to do themselves the job of tapping the 5G network traffic, by means of their own virtual TAP, and to forward clear traffic (not encrypted) outside of the virtual infrastructure, usually by means of GRE tunnels, with the goal to feed monitoring and security tools. The format and transport of these data are still not standardized, but this seems to be a promising way to overcome the issue.

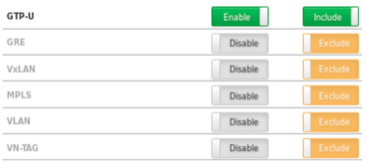
A-640 NPBs are a perfect choice to actively handle GRE and VXLAN tunnel. They act as an active tunnel endpoint, with their own MAC/IP setting, they do tunnel termination and inside tunnel filtering and load balancing. In summary, they get the info from the vTAP, and they aggregate, filter and load balance them to the monitoring and security tools.
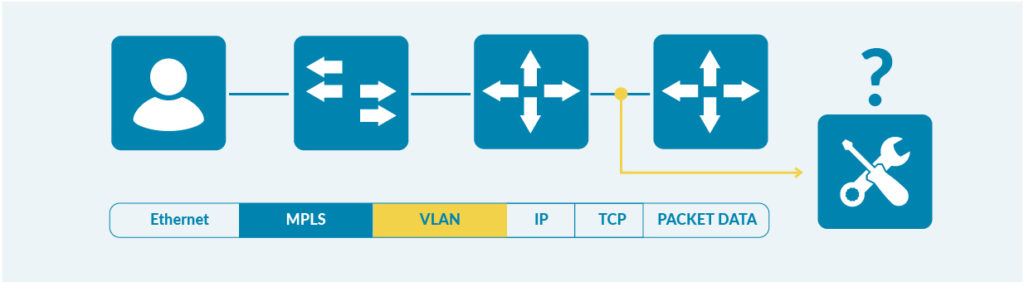
Additionally, the traffic sent by vTAPs can have multiple level of tunnels, since data coming from the virtual infrastructure are usually encapsulated using tunnels GRE, but also MPLS, VXLAN, VLAN, … in multiple levels: Microtel A-640 may strip partially or totally those encapsulations, in a configurable way depending on what the tools need, and filter and load balance original IP packets both on inner and outer parameters.