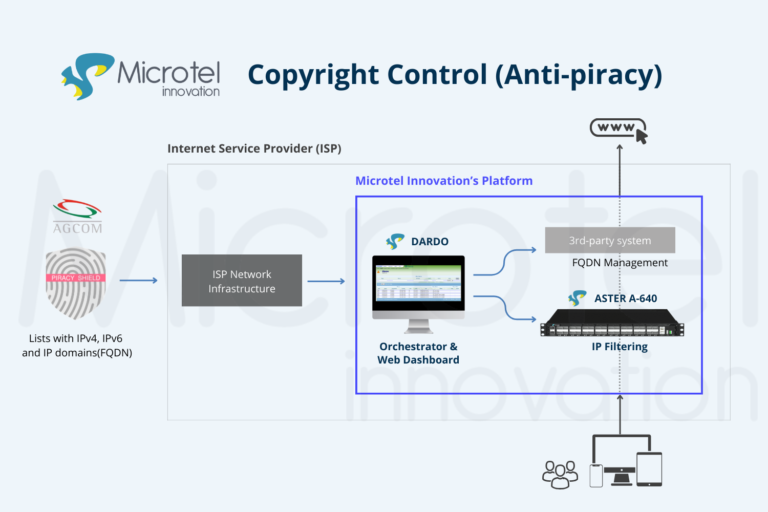
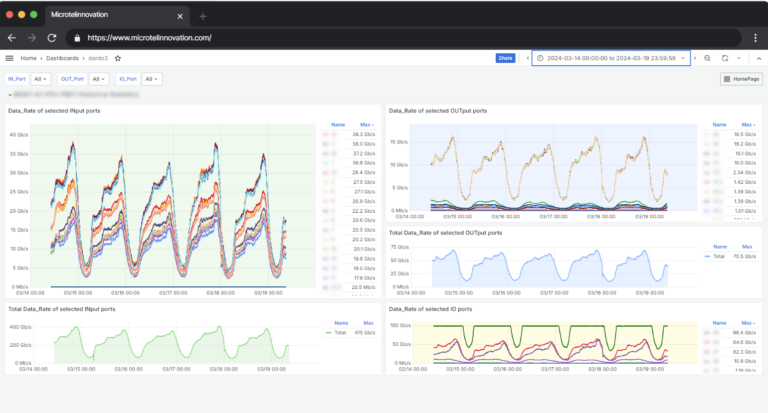
Mobile data traffic continues to grow exponentially, primarily driven by mobile video and over-the-top (OTT) services. While 5G has been widely introduced, its global deployment continues to expand, with existing LTE networks still handling a substantial portion of this traffic, and this demand is only increasing.
For operators, monitoring such high-volumes of traffic is critical for troubleshooting and ensuring optimal user experience. However, traditional solutions, such as adding probes or increasing their capacity, are costly and often impractical.
An alternative approach is to optimize the amount of User Plane traffic sent to monitoring tools. By reducing unnecessary traffic, operators can prevent infrastructure overload and ensure efficient resource utilization.
The Role of GTP in LTE Networks
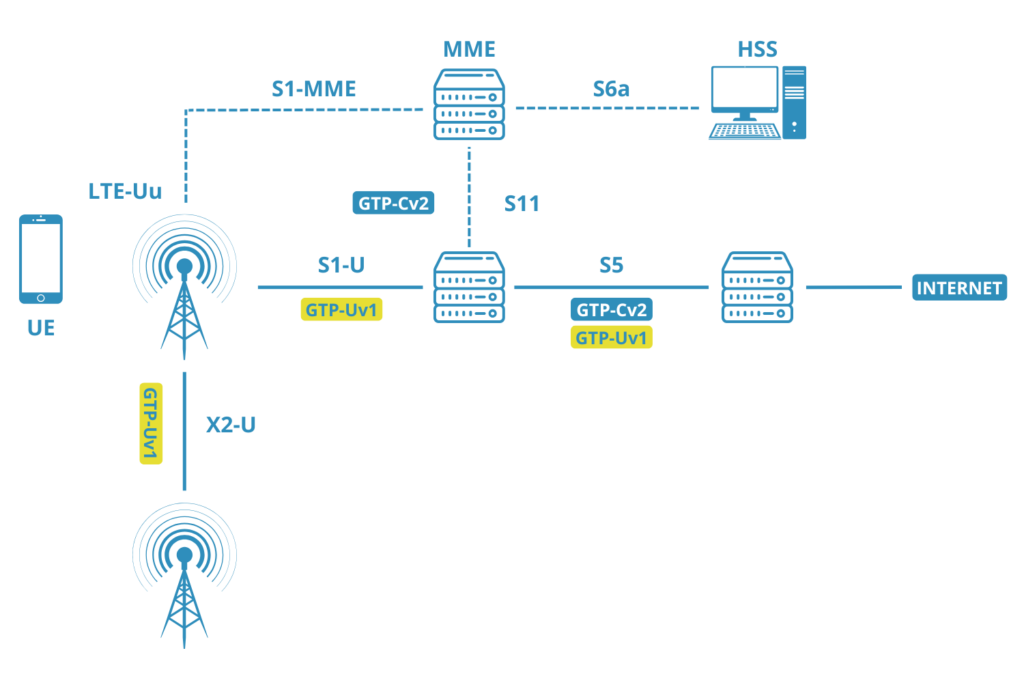
The GTP (GPRS Tunneling Protocol) is a key technology in 2G, 3G, and 4G/LTE networks. It carries both control-plane (GTP-C) and user-plane (GTP-U) data, enabling mobile data transfer across networks.
Addressing traffic challenges requires innovative solutions that filter and manage GTP-U traffic effectively without impacting performance.
The Solution
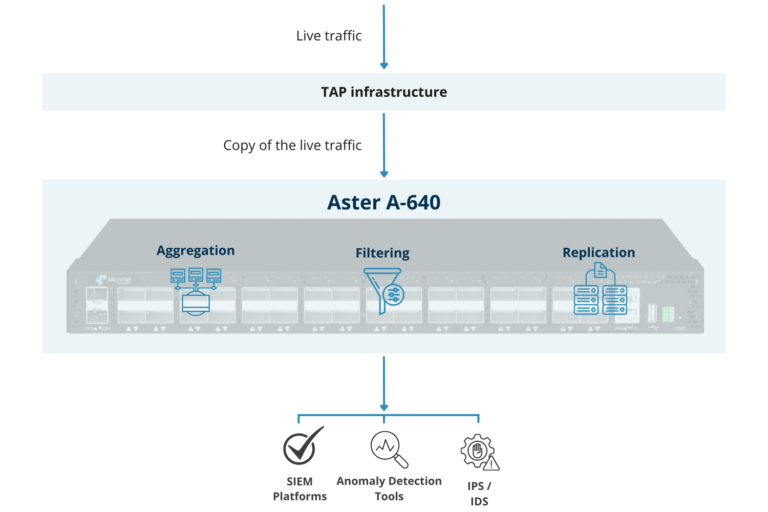
Microtel Innovation provides advanced Network Packet Brokers (NPBs) designed to reduce GTP User Plane traffic while maintaining optimal monitoring. Unlike traditional NPBs, which often lack sufficient computational power, Microtel’s solutions are built for high-performance demands.
The main techniques to reduce GTP User traffic are Inner IP filtering and filtering data based on different GTP-C parameters, both of which are described in detail in the following sections.
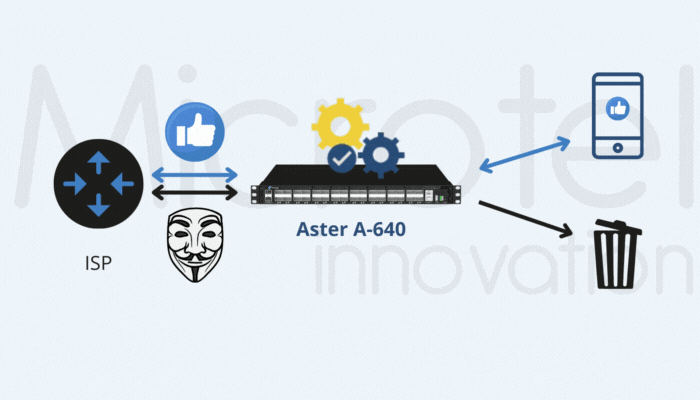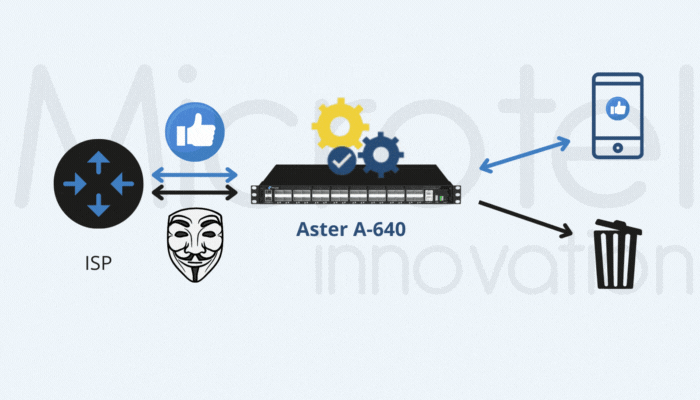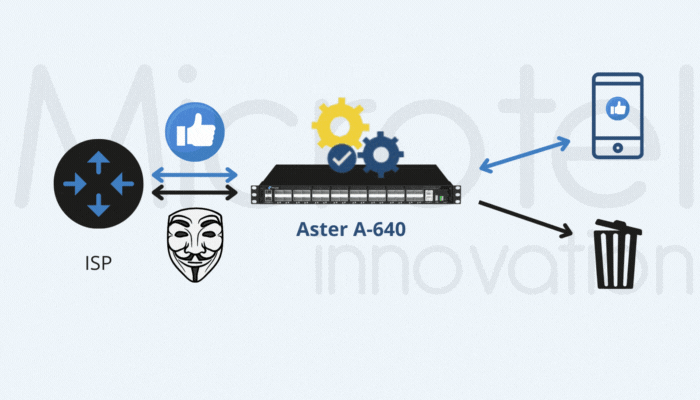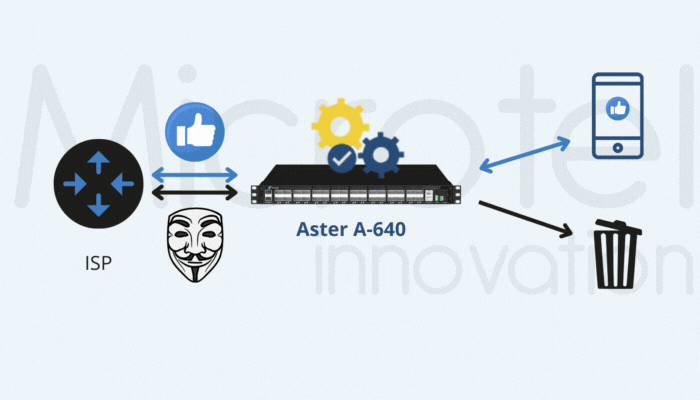
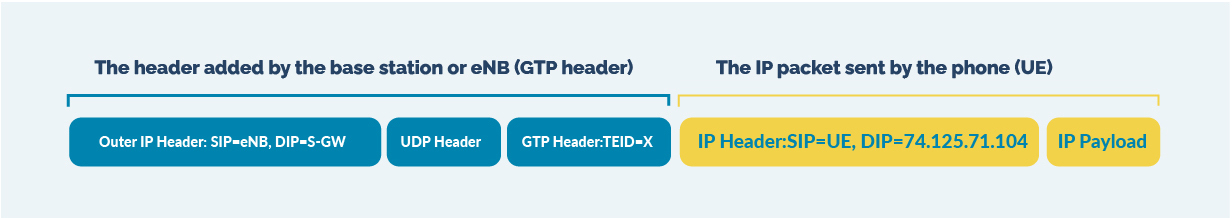
#1 | Inner IP Filtering for GTP-U Traffic Reduction
Inner IP filtering helps operators reduce traffic by targeting specific IPs within GTP tunnels. This technique requires hardware-based support to meet performance demands efficiently.
This technique can be effectively used in various use cases, represented in the table below.
| USE CASE | How | Notes |
|---|---|---|
| GTP User Plane traffic statistical sampling | Traffic is coherently reduced using inner IP filtering | In this case all traffic related to a specific inner IP is sent to the tools, but the number of inner IPs is sampled in order to reduce the traffic. Several reduction percentage may be configured, based on Operator specific needs |
| GTP User Plane traffic reduction by sending to the tools only the subscribers belonging to a specific list (IMSI - Inner IP dynamic correlation) | Use NPB Rest API to real time configure NPB Inner IP White List | Inner IP address is dynamic, can change in each PDP context message and is typically managed by the network itself. Operators which are able to real time trace the correlation between IMSI (unique identifier of the subscriber) and inner IP may real time configure NPB Inner IP White List using NPB REST API. |
| GTP User Plane traffic reduction by sending to the tools only the subscribers belonging to a specific list (IMSI - Inner IP static correlation) | Configure NPB Inner IP White List directly on the NPB | In some specific cases Inner IP and IMSI correlation does not change over the time. This is the case for example of mobile Set Top Box: they take advantage from the high bandwidth provided by LTE, maybe in an area where it is not easy to provide fibre connection to the home, but they are not moving. Connection is always on and IP address in this case usually does not change, depending on Operator policies. Operator usually have the list of Set Top Box inner IPs in their Data Base, so they can easily configure NPB to filter them. Also in this case REST API may be an interesting tool for the NPB to integrate with the Operator Data Base. |
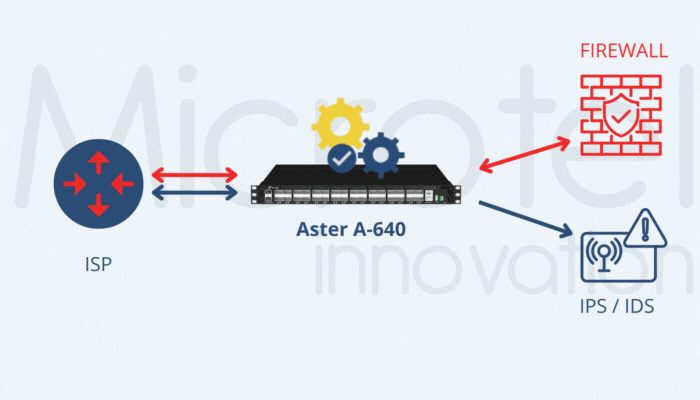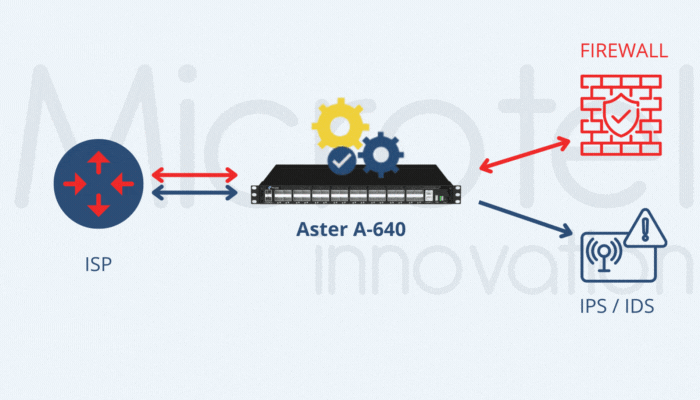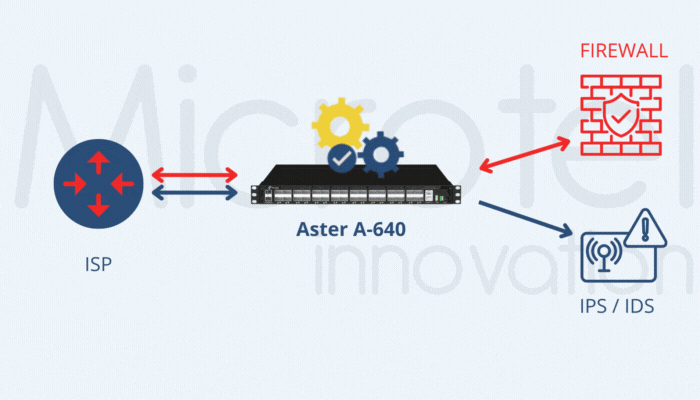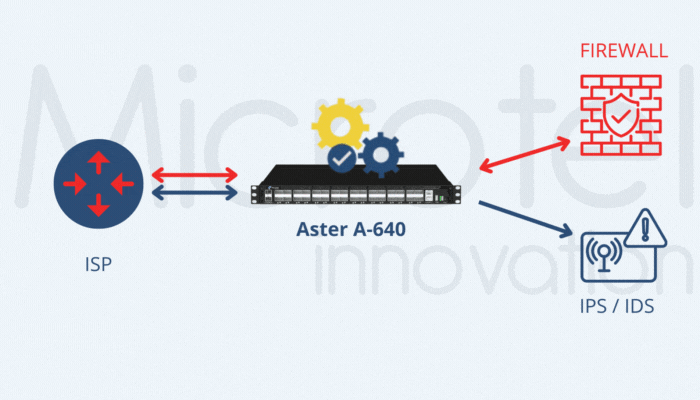
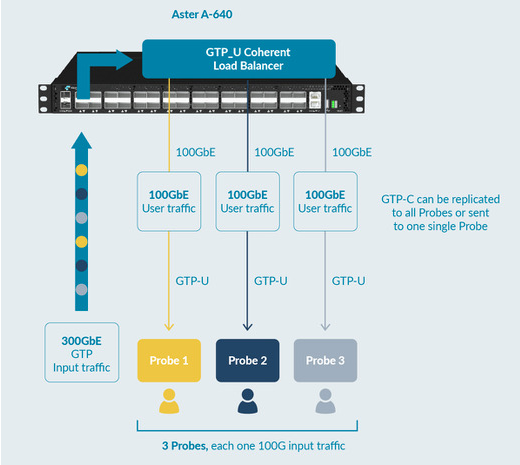
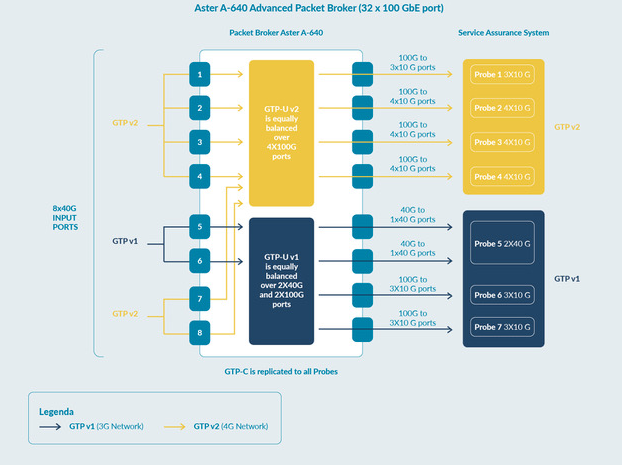
Microtel Innovation’s Aster A-640 and Aster A-648e appliances are specifically designed for these scenarios, offering hardware-based inner IP filtering and REST API support for integration with operator systems. This approach is also effective in architectures like CUPS and 5G, where GTP-C and GTP-U functionalities are geographically separated.
Optimize mobile traffic with innovative solutions for smarter, high-performance monitoring
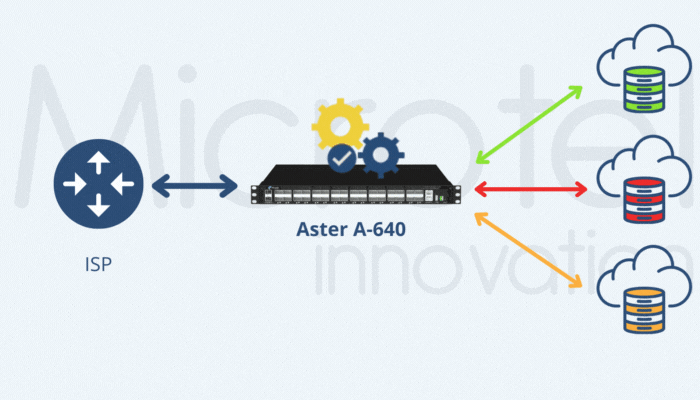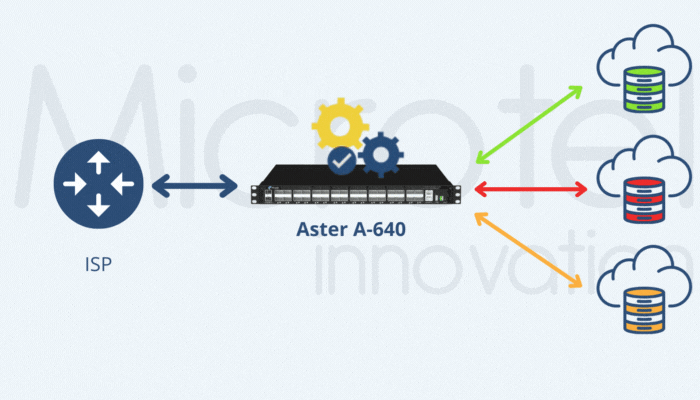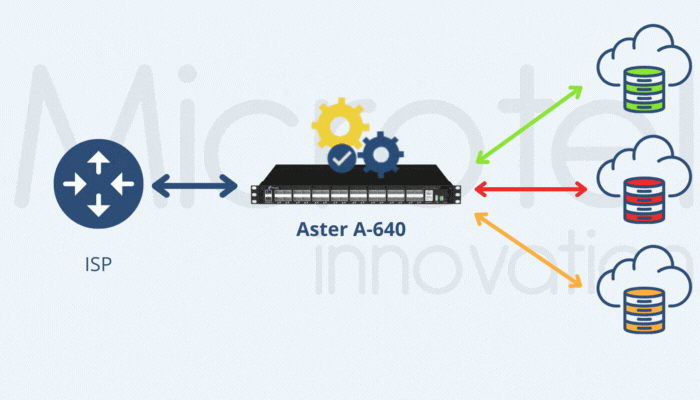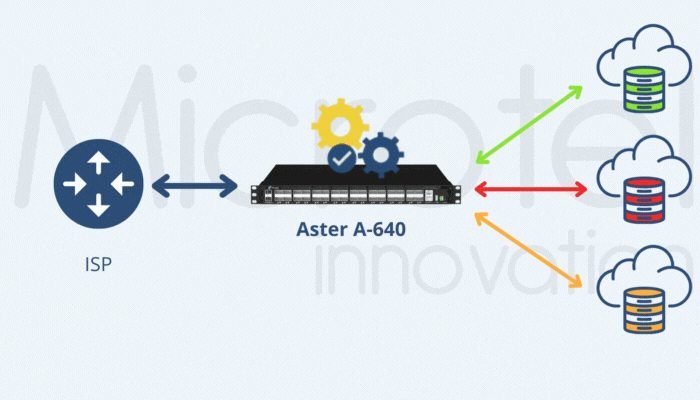
#2 | Filtering Based on GTP-C Parameters
Another effective strategy for reducing GTP User Plane traffic is filtering based on control-plane parameters, such as IMSI, IMEI, APN and geolocation data. These parameters are available in GTP-C packets, requiring correlation between GTP-C and GTP-U traffic. Microtel Innovation’s Aster A-XFE DEDUP appliances support this correlation at speeds from 1G to 100G, ensuring precise traffic management and subscriber-level granularity.
| Filter: mobile phone's IDS | How it works |
|---|---|
| IMSI (International Mobile Subscriber Identity) | User and/or Control plane traffic generated by IMSIs which are listed in the White/Black Lists is forwarded to the tools or blocked |
| MSISDN (Mobile Station International Subscriber Directory Number) | User and/or Control plane traffic generated by MSISDNs which are listed in the White/Black Lists is forwarded to the tools or blocked |
| IMEI (International Mobile Equipment Identity) | User and/or Control plane traffic generated by IMEIs which are listed in the White/Black Lists is forwarded to the tools or blocked |
| FIlter: Geographical location | HOW IT WORKS |
| User Location Information: ULI-CGI, ULI-SAI, ULI-RAI, ULI-TAI, ULI-LAI, ULI-ECG | User and/or Control plane traffic coming from geographical areas identified by the ULI-CGI, ULI-SAI, ULI-RAI, ULI-TAI, ULI-LAI, ULI-ECG which are listed in the White/Black Lists is forwarded to the tools or blocked |
| Filter: Network type | HOW IT WORKS |
| APN (Access Point Name) | User and/or Control plane traffic belonging to APNs which are listed in the White/Black Lists is forwarded to the tools or blocked |
| VoLTE (Voice over LTE) | User and/or Control plane traffic belonging to subscribers using VoLTE service is forwarded to the tools or blocked |
| RAT (Radio Access Technology) | User and/or Control plane traffic belonging to RATs which are listed in the White/Black Lists is forwarded to the tools or blocked |
| SER-NET (Serving Network) | User and/or Control plane traffic belonging to SER-NETs which are listed in the White/Black Lists is forwarded to the tools or blocked |
| QCI (QoS Class Identifier) | User and/or Control plane traffic which QCI is set with the values listed in the White/Black Lists is forwarded to the tools or blocked |
By correlating GTP-C and GTP-U traffic, these filters can dynamically ensure that only relevant traffic is sent to monitoring tools.
Conclusion
Efficiently managing GTP User Plane traffic is essential for operators facing increasing data demands. Microtel Innovation’s Aster Network Packet Brokers provide tailored, high-performance solutions to optimize monitoring and infrastructure usage. These advanced appliances address the evolving challenges of modern networks, ensuring cost-effective and scalable traffic management.